Month: August 2024
Behind AWS S3’s Scale
Comments
How to use iOS’s Live Text feature
Image: Samar Haddad / The Verge I’m something of a hoarder when it comes to interesting facts — I’ll see something online or in a photo, and a small voice in my brain says, “You’ll be able to use that reference somewhere, somehow. Save it so you can find it later!” Which is fine if … Read more
Amazon’s new Alexa voice assistant will use Claude AI
The new version of the voice assistant, dubbed “Remarkable Alexa,” is expected to launch in October and require a subscription fee. | Photo by Jennifer Pattison Tuohy / The Verge The improved version of Alexa that Amazon’s expected to release this year will primarily be powered by Anthropic’s Claude artificial intelligence model, according to Reuters. … Read more
Banks face new risks from permissionless blockchains, BIS warns
To mitigate risks associated with public blockchain networks, the paper proposed appointing an entity with the authority to “control and limit access” to cryptocurrency assets.
Epilepsy Protection for VRChat
Comments
Princess Zelda draws a sword in Echoes of Wisdom’s new trailer
Nintendo Our first couple of looks at Echoes of Wisdom made it seem like Zelda would be fighting to save Hyrule with just her wits and new magic powers, but the game’s latest trailer is all about the princess’ skills with a blade. Though Princess Zelda will wield a mystical staff that basically summons monsters … Read more
All the news on Telegram CEO Pavel Durov’s arrest
Image: Cath Virginia / The Verge, Getty Images French authorities arrested Durov as part of an investigation into criminal activity on Telegram. Continue reading…
Justin Sun taunts SUN token bears after 240% rally — SBF déjà vu?
The X post draws immediate similarities to a previous post of FTX’s Sam-Bankman Fried, back when the Solana token was trading at just $3.
New NFL Rivals Season Adds ‘Biggest Upgrade’ Since NFT Marketplace
Launching alongside the real-world season kickoff, the “Year 2” update will bring new features to NFT-enhanced mobile game, NFL Rivals.
9 months after SBF conviction, Peter Singer defends effective altruism in debate
According to the prominent voice for effective altruism, Sam Bankman-Fried’s version of the philosophy was only one among many.
Evolution After Revolution: How the Role of an IT Architect is Changing in the Modern World
When a company needs to construct a new building, an architect comes into play. This professional makes the important decisions: designing the structure, selecting the materials, and ensuring it meets the standards of comfort, convenience, and aesthetic appeal for both occupants and onlookers. In the IT realm, there are architects who perform a comparable role. … Read more
Toncoin hits $13.96B market cap amid Durov debacle
Toncoin reached a significant milestone with 1.1 million daily users, but its market experienced turbulence following the arrest of Telegram CEO Pavel Durov.
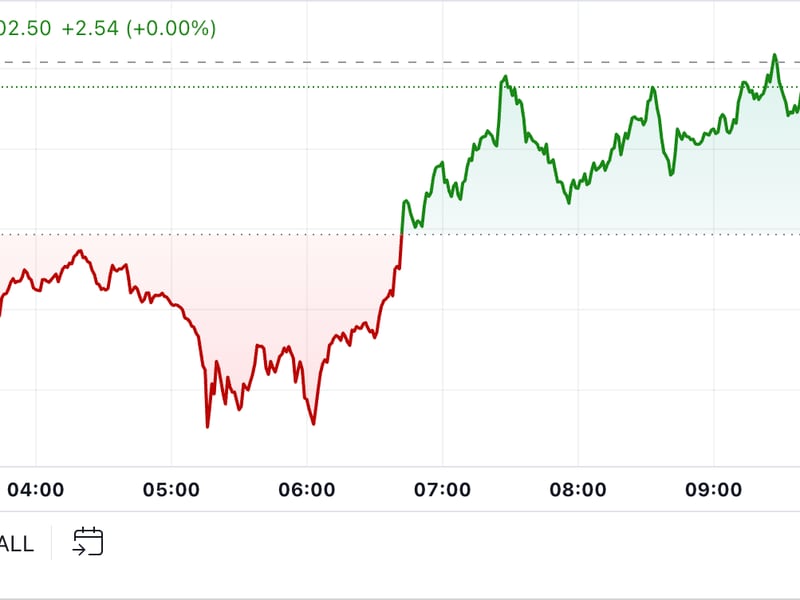
First Mover Americas: BTC Little Changed, on Course to End August Down 8%
The latest price moves in bitcoin (BTC) and crypto markets in context for Aug. 30, 2024. First Mover is CoinDesk’s daily newsletter that contextualizes the latest actions in the crypto markets.
Understanding Python Memory Efficiency: Tuples vs. Lists
When working with large datasets or optimizing the performance of your Python code, understanding how data structures consume memory is crucial. Two commonly used data structures in Python, lists and tuples, have significant differences in terms of memory usage. Let’s explore these differences with some Python code snippets and understand why tuples are generally more … Read more
Hackers Tapping into Company Systems to Test Security Features
In today’s rapidly evolving digital landscape, implementing SAST best practices to secure code is vital. It helps to identify and mitigate vulnerabilities. By adhering to these best practices, companies can strengthen their security posture and protect their systems against threats. It’s imperative to fully understand SAST best practices for secure source code. Since the source … Read more
AnandTech Farewell
Comments
How to Create Custom Annotations in Spring Boot
Such annotations fill the entire project in Spring Boot. But do you know what problems these annotations solve? Why were custom annotations introduced to begin with? How to create custom annotations? Today, I will cover: Why create custom annotations? What are the key benefits of using these annotations? How to create custom annotations? How does … Read more
Why You Shouldn’t Store Passwords in Your Browser: Password Security Risks
Storing passwords in your browser might seem convenient, but it comes with significant security risks. While browsers offer built-in password management features, they are not foolproof and can expose your sensitive information to various threats. Cybercriminals can exploit browser vulnerabilities, malware, or unauthorized access to your device, potentially leading to identity theft, financial loss, and … Read more
OpenAI searches for an answer to its copyright problems
You mean it’s all copyright? | Image: Cath Virginia / The Verge, Getty Images Why is OpenAI paying publishers if it already took their work? Continue reading…
How to Solve the Acute Skill Shortage of Highly Skilled AI/ML Workers
The Solution – Go for Vetted Recruitment Many Applicants – Need Higher Quality – Is This Your Company? There are plenty of candidates. But, with the high levels of pay, companies are fighting tooth and nail for the best employees. The best employees go to the stellar MAANG companies. There is a genuine shortage of … Read more
Toncoin and Notcoin Plunge Amid Telegram CEO Arrest and The Open Network Issues
Telegram-linked cryptocurrencies are down this week after Pavel Durov, the founder and CEO of the messaging app, was arrested.
Binance to support Cardano’s network upgrade
The Cardano network is ready for the Chang hard fork, part of the transition to the Voltaire era of decentralized network governance.
Evidence-Based Management in Business: Will it make a difference?
In the early 2000s, the concept of evidence-based medicine emerged. Dr. David Sackett defined it as using current best evidence in patient care decisions, and it has gained traction. Despite abundant research, only about 15% of medical decisions are based on evidence, with many relying on outdated knowledge, traditions, experience, and vendor information. Similarly, managers … Read more
The Next Revolution in Gen AI – Autonomous Dynamic Large Language Models
Can We Make Static Transformers Dynamic? Transformers are trained on the entirety of the visible Internet data. This helps them learn the statistical properties of human-generated data and makes them remarkably accurate in producing human-like data. But is that all? Can we improve upon them? Make them more human? Make them approach AGI even more … Read more